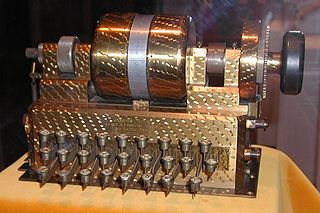
There is an interesting encryption technique using some hardware called "three rotor machine" or "The Enigma Cipher". The device was invented by the Germans during the II World War. There will be three rotors, to start with. The plain text will be typed in through the key board. When the first character is typed, it passes through the first rotor and gets encrypted according to the position of the rotor, because the rotor has 26 teeth, one for each alphabet. The first rotor passes it's output to the second rotor and the encryption takes place according to it's position, similarly with the third rotor. The new letter that we get for the plain text character, will be bounced off a reflector and we obtain at the first rotor.


The beauty of this machine lies in the complexity that it imposes by rotating. Initially, the first rotor makes its first move for the first character and the other two rotors remain stationary. Once the first rotor completes 26 moves, the second rotor makes a single move. Even now the third rotor is stationary. Till now, we have 26x26=676 combinations, coz the first rotor makes 26 moves for each of the 26 teeth in the second rotor. When the second rotor completes 26 moves, the third rotor makes a single move. The entire process repeats now. To sum it up, we have 26x26x26=17576 combinations.

The initial position of the rotors act as the key. The decoding people must know the initial configuration to decode the message. In those times, the configuration was written on a diary which had the configuration for each day. This was insecure, coz if someone happens to get the diary, he may form the machine of his own. The Enigma cipher was broken(decrypted secretly) by Alan Turing (In picture) and group of scientists for America. Had this not been broken, the Germans would have had a different course of war!


